March 27, 2023
A Four-Phase Approach to Procuring Cyber Liability Insurance
Ransomware attacks have nearly doubled since 2020, increasing the cost and requirements for purchasing cybersecurity insurance.
EXECUTIVE SUMMARY
Both the frequency and cost of ransomware incidents nearly doubled from 2020 to 2121. The Financial Crimes Enforcement Network (FinCEN) received 1,489 ransomware related filings worth nearly $1.2 billion in 2021. That is a 188% increase compared to the total of $416 million for 2020, and an average of four ransom incidents per day!
This increase in breaches and ransom attacks has made procuring cyber coverage exponentially more challenging. In turn, fewer providers are playing in the cyber insurance market, according to a new Sophos report: “With fewer organizations providing cyber cover, it’s a sellers’ market. They call the shots and can be selective about which clients they cover.” As the costs and requirements for purchasing cyber liability insurance continue to increase, organizations often ask: “Should I even buy cyber insurance? Is it worth it?” Answering these questions for your organization is crucial.
Even with rising premiums and the underwriting complications that come with more strenuous requirements in the current risk landscape, cyber insurance continues to be one of the most cost-effective ways for organizations to buy down risk. If a $2-million policy costs $50,000, $75,000 or even $100,000 per year (which would be extreme), that is still less expensive than many other risk-mitigation options. There are virtually no technical controls you could put in place for $50,000 that would result in a $2-million risk reduction. Most access control, detection, and response or prevention tools cost two to four times that amount, and it’s much more difficult to quantify the risk reduction gained by those tools
in dollars.
For larger organizations that require tens of millions of dollars in coverage, those costs start to shift, and provider-based insurance makes less sense. For those organizations, self-insurance options—which are covered later in this paper—may be a better fit. As the cyber insurance market continues to get squeezed by steeper losses it’s possible that those cost balances may shift, but cyber risk transfer is still a cost-effective strategy for now. Beyond that, the requirement for cyber insurance is becoming unavoidable. While insurance isn’t currently a requirement for any formal compliance framework, it is also becoming a third-party due-diligence requirement for many companies. As a result, requirements for certain levels of cyber coverage are increasingly baked into customer contracts and consequently corporate audits. So, even if cyber premiums do not provide sufficient ROI solely from a risk buy-down perspective, the cost justification can be bolstered by corporate compliance and client acquisition value.
The biggest prerequisite for effectively transferring or buying down risk, however, is assessing and quantifying your organization’s true risk to figure out where you stand in meeting policy requirements. This enables organizations to make improvements to their cyber defenses, which will directly impact an organization’s ability to secure the coverage they need.
Just as important, organizations must take a measured approach in selecting a policy. Buying policies can be complicated, and modern cyber insurance compliance requires that your organization learns how to navigate the lengthy and complex application process. Understanding the terms, coverages, requirements and exclusions is also key to ensuring that the policy you are paying for has the desired effect (i.e., you get paid in case of an incident).
This white paper discusses best practices along with what you need to know before procuring cyber insurance.
“With fewer organizations providing cyber cover, it’s a sellers’ market. They call the shots and can be selective about which clients they cover.”1
1Sophos: The State of Ransomware in Healthcare 2022
What You Don't Know Can Hurt You
There are six challenges that organizations tend to struggle with when trying to purchase cyber liability coverage.
1. Cost: When weighed against the potential reduction in risk exposure, are cyber liability premiums the best investment
of your cyber budget?
2. Application process: Do you understand all the questions being asked by the underwriters and how to respond appropriately to avoid claim denials or fraud allegations?
3. Identifying current cyber maturity: Do you know and can you articulate the current state of your cyber program? Is that information available for use in the application and risk assessment processes?
4. Not understanding coverage: Do you know how to interpret the policy legalese to understand which scenarios are and are not actually covered?
5. Inaccurately assessing coverage requirements: Do you understand what level of coverage you would need to reduce your risk exposure to a level within your organization’s risk tolerances, or do you just ask for an amount based on external factors like client information requests or a single underwriter’s limit determination?
6. Not properly measuring risk: Do you know your inherent risk, residual risk (based on challenge #4), risk appetite, maximum risk tolerance, and current risk exceedance? Those data points are key to accurately determining the coverage requirements in challenge #4.
These challenges all fall under one or more of the four phases of purchasing cyber insurance, which is the focus of this
white paper.
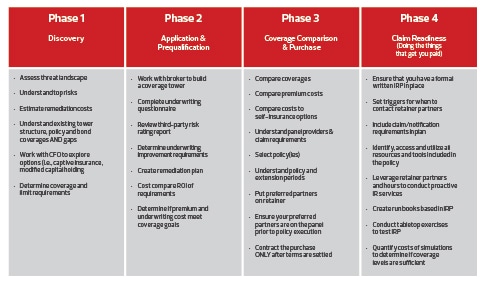
• Phase 1 – Discovery
• Phase 2 – Application & Prequalification
• Phase 3 – Coverage Comparison & Purchase
• Phase 4 – Claim Readiness
Four Phases of Purchasing Cyber Insurance
PHASE 1: DISCOVERY
ENGAGE BUSINESS STAKEHOLDERS
In order to determine your cyber liability coverage needs, you will need to understand your current coverages, risk exposure, risk appetite, and financial goals. The best way to gather all this information is to engage all the stakeholders as early as possible. Those parties may include the CFO, CRO, CISO, general counsel, and procurement team. The CFO in particular will be key to the successful completion of phase one: Discovery.
SELF-ASSESS
Risk management isn’t easy. Often, leadership sees it as an “advanced” cybersecurity capability, or they may think that it is simply out of reach for their enterprise. Performing self-assessment is critical not only to identifying the true state of your risk but also to providing visibility to leadership on where the enterprise stands on the coverability spectrum. What is the baseline of our cyber risk? What is our exposure? What is our risk appetite and maximum risk tolerance? These are the questions you need to ask to find out where you stand. Consulting with your CFO or CRO to determine where risk exceeds tolerance will determine if and how much risk you need to transfer, and that is the key to figuring out the solution that fits within your risk appetite.
Some things to consider during risk self-assessment:
- Understand top risks, threats, and controls gaps.
- Where possible, quantify your top risks and estimate remediation costs.
- If possible, determine whether your organization is underinvested or lacking the maturity required to obtain underwriting prior to filling out an application.
ENGAGE WITH ONE OR MORE CYBERSECURITY RATINGS COMPANIES
These companies specialize in calculating data-driven, objective and dynamic measurement of an organization’s security posture via a cybersecurity risk quantification or scorecard. Your scorecard will provide insight into what your security posture looks like to the outside world (i.e., providers), and help you proactively remediate, improve your score, and/or negotiate any findings with your provider.
PRO TIP: Insurance providers also use these third-party ratings to assess where you need improvement on your controls, so doing this puts you ahead of the game.
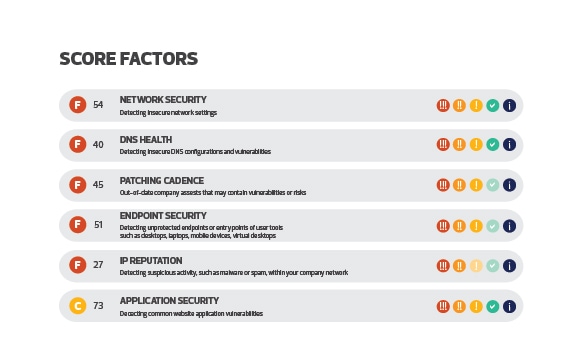
DETERMINE AND UNDERSTAND YOUR COVERAGE NEEDS
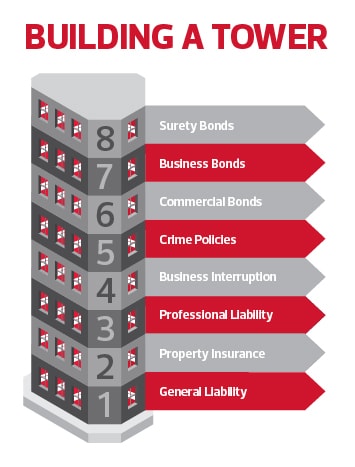
Cyber risk can be spread over a wide range of coverages including general liability, property, professional liability, business interruption and crime policies, among other standard coverages. Know what non-cyber coverage you have, including general liability insurance, commercial property insurance and business income insurance. Figuring out what coverage you already have will ensure that you’re not spending money you don’t need to on additional coverage. Work with your CFO to assess your options and identify your coverage targets (dollar amount per coverage item).
Once you understand what additional coverage you need, it’s time to engage your broker to build your insurance coverage tower. Your coverage tower is made up of multiple coverages from different insurance companies that create a solid and seamless coverage structure or “tower” to better ensure that your organization is protected in the event of an incident. Your broker can help you spread out the coverage you need according to the options available to you while also helping you hit your coverage targets in alignment with your business’s financial goals.
Larger firms have started to treat cyber liability acquisition like the procurement of any other product. Using an RFP-style process to request bids for coverage can create a competitive situation that often helps reduce the underwriting back-and-forth.
PRO TIP: You have options. A lot of businesses don’t know or consider other alternatives to provider coverage if it’s determined unfeasible. These alternatives can include commercial, business and surety bonds as well as self-insurance, captive insurance, and capital holdings.
PHASE 2 – APPLICATION AND PREQUALIFICATION
After discovery and self-assessment (and remediation), you’re ready to apply for your coverage quote. Your broker will provide you with a coverage questionnaire/application. Consider this application an additional assessment. If some of the answers to the questions in this application are “no,” you might be tempted to go to another insurance company to avoid addressing the provider’s requirement. It’s to your advantage to leverage this application and take the opportunity to level-up your controls and make the improvements necessary to get the coverage you need.
Make sure that you answer all the questions in the application as fully and truthfully as possible. Incorrect or untruthful answers can be grounds for claims denial or, worst-case, insurance fraud! If there’s a question you don’t have the answer to, figure out the right answer before submitting your application. That may mean additional remediation. Don’t fall subject to insurance fraud by filling in an answer purely for the sake of completing the questionnaire. It’s becoming increasingly popular for underwriters to use absolutist language in these application questionnaires. Terms like “always,” “never,” “all” make it increasingly difficult to truthfully respond in the affirmative to these queries, and require organizations to amend their responses with details about their exception policies and compensating controls. You are also generally not required to submit your responses on the provided form. More and more organizations are copying application questions into a Word document where they can append yes and no questions with additional qualification information. It would be highly unlikely to see a broker, provider or underwriter reject that type of response, and that additional disclosure informs the underwriter’s risk calculus and helps shield you from claims denials.
If you’re unsure how to draft appropriate and factual responses to application questions, it may be wise to engage third-party assistance from security solutions specialists like CDW, whose experts understand policy language and can help craft appropriate responses.
Once you’ve submitted your application, the underwriter may respond with any additional controls they want you to have in place.
CYBERSECURITY CONTROLS
The key to insurability, mitigation and resilience is preparation. Start preparing for the underwriting process early. Without responses in the top control categories, coverage offered and insurability may be in question. Evaluating your cybersecurity maturity against these top controls will help you identify where improvements are needed. You cannot be too prepared. With that in mind, you should expect that the underwriting process will be rigorous and require you to answer progressively more detailed questions from underwriters.
TOP CYBERSECURITY CONTROLS YOU NEED TO HAVE IN PLACE
It is common for the underwriter to “request” that you make controls improvements. Those may include, but are not
limited to:
- MFA: Multifactor Authentication across all remote access
- PIM/PAM: Priviledged Identity/Access Management
- RA: Remote Access; user access controls to company resources including VPN, ZTNA, SSO...
- EDR: Endpoint Detection and Response
- SIEM: SIEM/Logging/Detection
- IRP: Incident Response Plan
- BCP/DR: Business Continuity Plan/Disaster Recovery
- Backup Strategy: Secured encrypted vulernability management
- Email Security: Reduce the impact of phishing; protect the confidentiality and integrity of data and messaging
- Security Awareness Training: Ongoing security training
- TPRM: Third-Party; Risk Management
- Cybersecurity Ratings: Improvement to cybersecurity ratings
PHASE 3 – COVERAGE COMPARISON AND PURCHASE
COMMON CYBER COVERAGES
Cyber coverages include both first-party and third-party hazards. First-party cyber liability insurance helps you respond to data breaches on your own network or systems. Third-party cyber liability insurance helps pay for lawsuits caused by data breaches on a client’s network or systems. Clarification: this coverage is paid to you in either situation, whether it happened directly to you or happened to a partner and impacted you.
First-party coverage typically includes:
- Cyber incident response
- Extortion
- Business interruption (e.g., system failure, denial-of-service attack, customer attrition loss)
- Digital data loss/recovery
- Cybercrime (e.g., computer fraud, funds transfer fraud,
invoice fraud) - Social engineering fraud
- Reputational loss (e.g., brand restoration, adverse media publication, review bombing)
Third-party coverage typically includes:
- Breach liability
- Payment card loss
- Regulatory proceedings
- Media liability
- Vendor/technology errors and omissions
- Outsourced provider business interruption
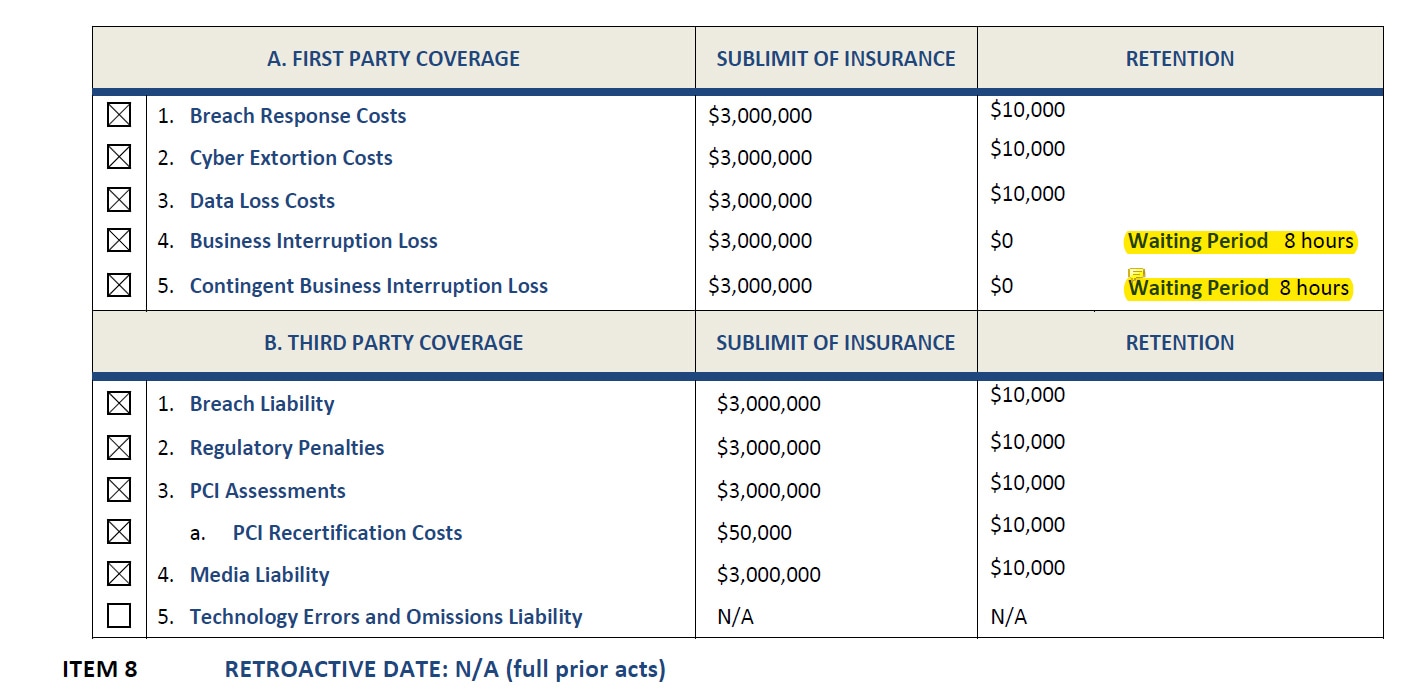
Insurers will often break out and quantify separate coverage limits, retentions (deductible), and waiting periods for each of these items.
UNDERSTANDING POLICY LANGUAGE
It’s important to understand policy language, because a $2-million cyber liability policy doesn’t necessarily cover every loss scenario to the full $2 million. Which events have lower limits, higher retentions, or are completely excluded are all defined in policy language that is often hard to read and understand. It’s not uncommon for organizations to be surprised when they attempt to file a claim and discover that they aren’t covered as well as expected, and aren’t getting what they thought they were paying for. Again, engaging a security firm that understands policy language can help, but below are some terms you should be familiar with and look out for.1
Acts of War/Terrorism: Almost all insurance policies exclude coverage for losses or damages caused by acts of war or terrorism. This has changed recently in the wake of the Mondlez and Merek cases. According to the New York Times, both organizations tried to file claims under their all-coverage policies for losses stemming from the 2017 NotPetya attack. Since NotPetya originated as a Russian attack on Ukraine, their carriers denied the claims under the Acts of War clause. While those companies did recently win settlements, those cases haven’t 100% settled what constitutes an act of war; those cases fell in favor of the victim companies since the policies didn’t explicitly identify cyberattacks. That exception wouldn’t apply to cyber liability policies, and providers are now adding the cyber language to most Acts of War exclusions. It’s important to understand what language is included in the war exclusions across all your policies to ensure that you are covered in the event of direct or indirect nation-state action.
Sublimit: A limitation in an insurance policy on the amount of coverage available to cover a specific type of loss. A sublimit is part of, rather than in addition to, the limit that would otherwise apply to the loss. (Sublimit vs. aggregate limit: a $3-million policy may have a lower $250,000 sublimit for cybercrime).
Retention: Essentially a deductible. Some are single per claim; some are aggregate per coverage.
Waiting Period: Duration of outage before a claim can be made. Often eight to 10 hours, meaning a one workday outage isn’t covered.
Extended Reporting Period (ERP): A designated time period after a claims-made policy has expired during which a claim may be submitted and coverage triggered as if the claim had been made during the policy period.
M&A Coverage or Representation: A form of coverage designed to guarantee the contractual representations made by sellers associated with corporate mergers and acquisitions. Some policies automatically cover entities you acquire; some allow you to add those named organizations for a nominal fee; some exclude acquired organizations altogether.
Retroactive Date: A provision found in many (although not all) claims-made policies that eliminates coverage for claims produced by wrongful acts that took place prior to a specified date, even if the claim is first made during the policy period.
Full Prior Acts: A type of claims-made liability policy that does not contain a retroactive date and therefore covers claims arising from acts that took place at any time prior to the inception date of the policy.
Duty to Defend: An insurer’s obligation to provide an insured with defense to claims made under a liability insurance policy. As a general rule, an insured need only establish that there is potential for coverage under a policy to give rise to the insurer’s duty to defend.
When a lawsuit involves some claims that are covered by a cyber policy and others that are not, a question often arises: What portion of the policyholder’s defense costs must the insurer pay? Some provisions are more advantageous to the policyholder than others. For example, some policies say that the insurer will pay all defense costs if the lawsuit alleges any claim that is potentially covered. Others stipulate that the insurer will only pay the costs that it unilaterally believes to be covered until a different allocation is negotiated, arbitrated, or determined by a court.
These issues are less likely to arise under a “duty to defend” policy, where the insurer must assume the defense of any third-party claims. This type of policy typically covers all defense costs if any of the claims are potentially covered. However, under a “duty to reimburse” policy, where the insurer agrees to reimburse the policyholder for its defense costs or pay them on its behalf, allocation is more likely to be disputed.
Duty to Pay/Reimburse: An insurer’s obligation to pay defense costs but without duty to defend.
Partial Subrogation Waiver: A subrogation waiver waives the insurer’s right to subrogate or take legal action against a third party that’s responsible for the loss of the insured in case of a breach. With a partial, the insurance company will not declare that its rights are impaired by an agreement that you signed before the breach (contracted liability limits).
If your insurer pays a loss, it may become “subrogated” to your claims against any third parties that were responsible for causing the breach. This means that the insurer can try to recoup its payment to you by pursuing your claims against the responsible parties. One problem with such provisions in the cyber context is that contracts with data management vendors commonly include provisions that limit their liability. In such cases, your insurer may claim that you have breached your insurance contract by impairing the insurer’s recourse against the culpable vendor. A possible fix is to insist that a partial “waiver of subrogation” provision be added to your cyber policy. These provisions, which are common in other lines of coverage, provide that the insurer will not assert that its subrogation rights have been impaired by any contract you entered into before a loss occurred. Some insurers are willing to agree to such provisions in the cyber context, but others may not be. If your insurer is not willing to give a partial subrogation waiver, you should consider shopping elsewhere.
Extension Period: If you choose to cancel your policy, you can sometimes pay a multiple of your premium to be able to claim events that are discovered later but occurred during your coverage period. This can be important if your new policy doesn’t cover full prior acts.
Right to Audit: It’s increasingly common to see providers include requirements for regular audits and penetration testing. This can usually be performed by a third party of your choosing as long as that company isn’t also providing you a managed security service. Some providers will include provisions that allow their firm or selected third-party auditors to assess your program or environment to validate the controls and risk exposure you represented in your application. This provision can be periodic, annual, or triggered by an event.
UNDERSTAND EXCLUSIONS
Broadly written exclusions can undermine many of your key reasons for obtaining cyber insurance in the first place. Exclusions of special note here may include Breach of Contract, Physical Destruction of operational technology (OT), and Officer Liability. Make sure that you negotiate Physical Destruction of OT and coverage for your officers into your coverage contract, or that you have these covered by a separate policy. The verdict in the 2022 ex-Uber CISO case reinforces the need for officer coverage. Officer coverage needs to be both named and positional. Positional coverage covers C-level officers while they are in their roles within the company, and named coverage identifies executives by name for coverage after they leave the organization. Obviously, Officer Liability coverage helps shield against civil but not criminal cases like United States v. Joseph Sullivan.
Some policies broadly exclude coverage for any liability arising from a breach of contract. Many organizations collect and store confidential information from customers, patients or business partners under contracts that require them to maintain confidentiality. They buy cyber insurance precisely to protect themselves in case a privacy breach gives rise to claims for damages under these confidentiality agreements. It can be intentionally difficult to get the brokers and providers to clarify vaguely written exclusions, but you can get your legal team to redline exclusions so you can at least attempt to understand what you are agreeing to.
Ensuring that your program is claim-ready and aligned with your policy is covered in phase four; however, it is important to discover and understand the claims language within your terms in advance of signing on the dotted line.
The following terms are generally included in the policy definitions, but it’s increasingly common to find additional claims info on things like panel partners, hotlines, filing forms, etc., outside the policy document, either in separate files or on the provider’s website. All of those ideas are further discussed in phase four.
Providing Notice: It is recommended that you work with your legal team to determine when you want or need to notify the insurer (especially if you don’t end up making a claim) to determine what constitutes a “reasonable time period” for providing notice since non-disclosure can result in claim denial. You should also review the language around notification requirements for potential claims to determine if your policy contains a clause stipulating your “duty to disclose” events for which you do not intend to file a claim.
Period of Restoration: Loss and costs resulting from a breach are generally covered only during the Period of Restoration, which is typically 120 days, meaning costs that run past a quarter are not covered. This can often be negotiated out to 180 days or more.
Once you parse and understand the terms of your policy, you will likely discover that some terms don’t meet the requirements you defined in phase one. When this happens, don’t forget: everything is negotiable.
NEGOTIATE
On that note, you can negotiate and redline nearly every part of a policy, but you must do it prior to purchase. This is a contract. In the same way you would have your legal team redline a contract, you can redline an insurance policy. That doesn’t mean that underwriters and providers will agree to these terms, but your broker can often help guide you toward those terms to which individual providers are most amenable.
As discussed in this white paper, common negotiation points include the following:
- Coverage types
- Underwriting requirements
- Sublimits
- Prior acts
- Subrogation waiver
- Length of restoration period
- Exclusion language
- Panel providers
- Waiting periods
- Duty to defend
- Premium cost
- Retention cost
PHASE 4 – CLAIM READINESS
The terms of your policy will also include details about the process of filing claims. Ensuring that your organization is claim-ready and your response activities are aligned to the claims process are keys to actualizing the value of your insurance investment in the event of an incident.
Aligning your formal incident response plan (IRP) with your policy is vital to getting your claim validated. Make sure your IRP includes the things that get you paid in the event of an incident. For example, if your policy includes a breach hotline, then including guidance in your IR plan and playbooks around if and when to call that hotline will be a key part of the plan.
PRO TIP: Make sure you’re not leaving free resources on the table. Many cyber insurance providers contract to offer their policyholders access to online portals full of risk reduction, IR planning, vulnerability management, and other readiness tools. Some providers offer annual premium rebates for cyber improvement projects. These resources can generally be found in the policy terms, but sometimes you have to go looking for them on the provider’s websites.
UNDERSTANDING PANEL PROVIDERS
An insurance panel is a collection of service providers that an insurance company will pay for services for their customers. It’s also called credentialing, and each insurance provider selects its own panel.
The brokers and providers have started to position their panel partnerships as a value-added benefit and suggest that there are cost and overhead benefits in not having to contract and retain response partners. However, it is still best practice to build your own panel team because your insurance provider’s partners might not always be functioning in your best interest.
This idea can be clarified by applying this logic to other types of insurance. If your house burned down, you probably wouldn’t call your insurance carrier and ask them to come to the table with the fire marshal, ask them to help you find a builder, and get their input about your blueprints and building plans. So waiting until an event happens to have a provider randomly “assign” resources via hotline or even point you toward a list of providers you haven’t previously contracted with can be an extra burden at an already complicated time. Not onboarding your panel partners in advance can be a huge hindrance since just executing contracts, MSAs and NDAs can take days or weeks—especially since these types of contracts are usually executed as a tri-party agreement with you, the partner provider, and your external legal firm. You generally can’t wait that amount of time to begin response activities. The result would be either that you are forced to rapidly agree, or to take on work at risk.
Further, ensuring that your forensics partner can access your data and leverage your tool stack is key to a quick response. Breaches where organizations needed to procure and/or roll out thousands of endpoint agents before the IR partner can begin their investigation are not unheard of. Beyond that, major cyber incidents require a lot of internal and external stakeholders to work together as a team; like any team, they need practice to perform well. Knowing your partners in advance and including them in your playbooks and tabletop exercises can help ensure that your IR is smooth and that your program is claim-ready.
Again, policyholders are generally not obligated to contract for services with the insurer’s panel providers. Even though insurers would prefer that you use their panel providers, you can almost always arrange for your preferred partners to be added to the panel for your policy. You do generally need to make that request before executing your policy, and they will need to adhere to the policy provider’s requirements for rates and coverage.
PUT RETAINERS IN PLACE
If you opt to select your own partners in advance, one of the best ways to ensure that your partner team is appropriately on-boarded is to put those partners on retainer.
Your response team should include partners for forensics, incident response, third-party legal, a breach coach, and public relations—but you don’t necessarily have to select one of each. You can select your own legal and forensics partners and let your provider help you find a breach coach or comms specialist if the need arises.
The benefit to putting your own retainers in place is, of course, that you get to choose who you prefer to work with, not someone the insurer prefers to work with. Having retainers in place also means you’re doing your due diligence to work with a team that is familiar with you and your business. Being helped by a team of people who are actually on your team is well worth the additional cost to your coverage.
Incident response retainers should include:
- A Service Level Agreement (SLA)
- A block of hours (active/proactive IR)
- The ability for unused hours to be repurposed
- An onboarding plan to ensure that legal paperwork is in place in advance
- A break-in-case-of-emergency playbook to engage the IR partner
COORDINATE WITH LEGAL
While you should engage your general legal counsel back in step #1 (Discovery), it is important to ensure that your legal team remains aligned with your formal incident response plan. In-house counsel is great for proactive IR activities like procuring policies and setting up, but in your response program you will likely want to engage third-party external counsel for any reactive IR activities. Leveraging your third-party counsel to work as an intermediary to your IR and forensic partner can provide a layer of attorney/client privilege that could be vital if your incident were to lead to litigation. Additionally, your in-house legal team most likely won’t have cyber breach experience; you will want to find a firm that can provide you with breach coaching.
Even though cases like the E.D. Virginia Capital One ruling limit the extent of attorney/client privilege around forensic reports, it is still best practice to have all of your IR contracts, statements of work, retainers, etc. executed as tri-party agreements where your external counsel contracts with the partner provider on your behalf. It is important to note that attorney/client privilege is initiated by your attorney and includes only legal advice or communications, not facts such as the timeline of breach events.
RANSOM BROKERS AND EXTORTION PAYMENTS
One of the key reasons organizations take on cyber insurance is to help cover ransom payments in the event of extortion attacks. Ransomware accounted for 75% of all cyber claims in 2021, according to a cyber insurance industry report from AM Best. It’s common for insurers to make extortion payments; but even though it is an option, paying extortion should still be considered last among the list of options and should be taken on as a business decision. Extortion payments should be decided on a case-by-case basis by executive leadership, legal counsel, breach coach, IR firm, and broker, and only after they understand the payment risks.
The risks of extortion payments include:
- Non-recovery from double encryption or restore failure
- Additional demands across multiple extortion vectors
- Legal sanctions violations
- Repeat targeting
- Bolstering the ransomware economy
Also, extortion payments should never be made in an attempt to cover up an incident.
If you choose to pay ransoms, DO NOT include ransom payment specifics in your written incident response plan. When an organization is writing down their formal IRP and aligning it to their policy, they may be tempted to write down plans for paying ransoms, obtaining/storing crypto to facilitate extortion payments or engaging/retaining brokers. Those things should NOT be included in your formal IRP. You should not be planning in advance to be breached and to pay ransoms—it would be hard to explain in court why your plan to protect your customer/employee/business data included plans for paying
a ransom.
If you find that you do need to make a ransom payment, your insurance provider or breach coach should be able to help you engage a ransom broker. Ransom brokers can help you negotiate payments including the cost, terms and deadlines. The broker will also facilitate the payment and the decryption key exchange to help ensure that everything works as expected.
It’s becoming common for threat actors to threaten data or encryption key deletion if victims involve brokers and/or law enforcement. That should not deter you from engaging a broker for assistance. If you do engage a broker, be sure to choose a reputable firm recommended by your provider or law firm. Recently, many ransom operators have started pushing victims toward their “preferred partner” brokers because they have pre-negotiated discounts and payment details. One Darkside operator said in an interview with Recorded Future “Recovery companies we work with only simplify the process. They have their own personal discounts that can vary between 20—40% and the entire recovery process takes no more than 24 hours from the moment of the first contact.”
Even though cases like the E.D. Virginia Capital One ruling limit the extent of attorney/client privilege around forensic reports, it is still best practice to have all of your IR contracts, statements of work, retainers, etc. executed as tri-party agreements where your external counsel contracts with the partner provider on your behalf. It is important to note that attorney/client privilege is initiated by your attorney and includes only legal advice or communications, not facts such as the timeline of breach events.
PRO TIP: Be sure to effectively “hide” your insurance policy policy and IRP from bad actors. They are often prime targets for ransom groups because they provide a lot of valuable information, including exactly how much they can ask for.
Conclusion
As long as the current ransomware landscape persists, obtaining cyber liability insurance will be an increasingly difficult and costly endeavor. Even so, cyber insurance continues to be one of our better options for buying down IT risk. Additionally, requirements for cyber insurance are becoming more and more common in audits, third-party due diligence, and B2B contracts. That means we are going to be dealing with these insurance procurement woes for the foreseeable future. As such, it’s in your best interest to make sure that your coverage is right-sized and that you are doing your best to ensure that you are getting what you pay for. The best way to do that is to follow an insurance procurement framework like the one laid out in this white paper. The four phases of purchase are summarized in the chart below for quick reference:
When in doubt, you can engage a security firm like CDW that can provide a pre-packaged approach to all four phases or assist with any of the phases where needed—from risk quantification to application preparation, policy selection, or incident response alignment.
Learn more about CDW’s security advisory services here and CDW’s Incident Response Services here. You can also continue the conversation with the CDW Field CISO team at securityadvisors@cdw.com.
Story by Walt Powell, an accomplished cybersecurity expert and executive coach who specializes in providing executive guidance around risk, governance, compliance and IT security strategies. He is the executive security strategist at CDW and prior to that served as a senior security advisor at Optiv and a virtual CISO at Left Brain Security. Through these roles, he has had the opportunity to learn from and contribute to hundreds of CISOs and their programs. Powell holds dozens of professional certifications including CISSP, CISM, Carnegie Mellon – Heinz CISO, and the Stanford Advanced Cybersecurity Certificate, along with countless technical and presales certifications from top security vendors. Powell is also an accomplished musician and father who loves to spend time with his kids.
Walt Powell
Lead Field CISO
