September 27, 2019
Take a Process Approach to Cybersecurity
Assessing your current security posture can prevent missteps as you move forward.

In December 2018, I received a phone call from a regular customer making a common end-of-year request. “I have some leftover money in my cybersecurity budget,” he said, “and I need to spend it before the end of the year or I will lose the funding. Could you put together a quote for a new pair of next-generation firewalls?”
I knew that my customer had already made significant investments in perimeter protection, so I took the opportunity to chat with him about his motivation in looking for a new solution. It quickly became apparent that he was under pressure to spend his security budget to demonstrate that the team was committing resources to protect the organization against cyberattacks. I suggested that the organization take a different approach that might satisfy his need to show a commitment to security while avoiding the purchase of an additional complex and expensive technology solution.
Meet Security as a Process
I’m a firm believer in taking a process approach to cybersecurity. Instead of simply purchasing the latest and greatest security product, the process-based approach uses an organized and repeatable technique to optimize the use of limited cybersecurity resources. That’s what my customer chose to do early this year.
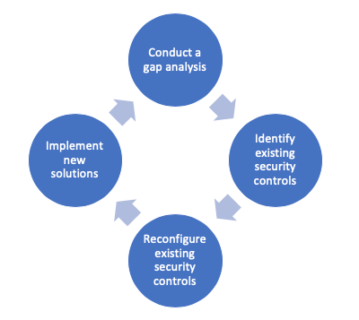
This process begins with a comprehensive gap assessment. This assessment combines several of CDW’s consulting services to provide customers with an independent look at their security postures. CDW analysts conduct vulnerability scans, review architectures, conduct penetration tests and incorporate threat intelligence information into their work. The result is a set of recommendations for improving an organization’s technical controls and business processes for cybersecurity.
SPOT SECURITY GAPS: Explore CDW assessment services.
Put the Process to Work
My customer and I worked through this gap analysis process and identified a gap in the organization’s firewall security controls. The company had installed its existing firewall two years earlier and had made several changes to the firewall rules. A handful of those changes created a hole in the firewall’s security posture, allowing external access to some test and development systems. We realized that this was a major security risk, as those systems weren’t subject to the same level of security scrutiny as production systems.
This moved us into the next phase of the assessment. We performed an inventory of the company’s existing security controls and realized that the firewall it already had in place was perfectly capable of addressing the threat, and a new purchase wasn’t necessary. We then reconfigured the existing firewall to address the gap identified during our analysis.
This quick correction allowed us to avoid the last phase of the process: implementing new security solutions. The retailer’s existing technology was more than sufficient to protect the network — it just needed a slight configuration tweak. This saved the company more than just money; it also improved the efficiency of the IT staff by minimizing the number of security products requiring their attention.
My customer was elated. He now had a CDW assessment in hand that he could take to his leadership and show that the IT team was operating in line with cybersecurity best practices. And he was able to achieve this objective for about 10 percent of the cost of acquiring the new firewalls that he originally called about. That’s a great way to show clear value to the business.

