How Vulnerable is Your SCADA System
Make sure you have the powerful multilayered defenses you need to keep determined cyberattackers at bay.
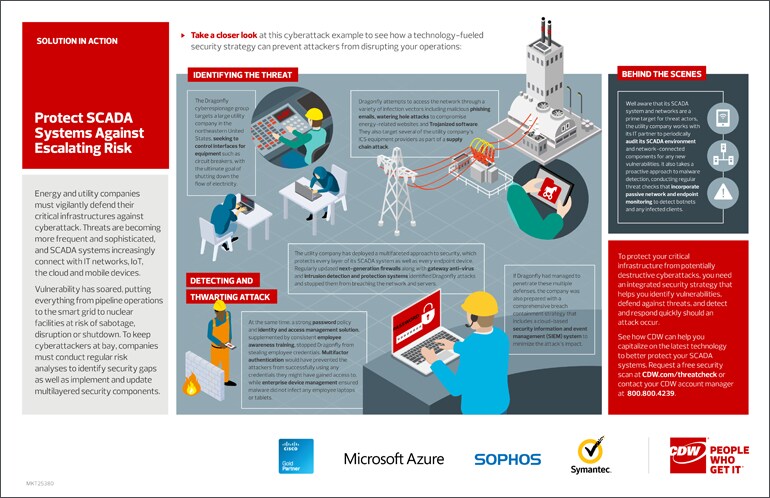
The risk of sabotage, disruption or shutdown of energy and utility operations has climbed precipitously as SCADA networks become increasingly interconnected with IT networks, IoT, the cloud and mobile devices.
Effectively protecting critical infrastructure from sophisticated cyberattack groups such as Dragonfly requires a comprehensive, multilayered security strategy that enables companies to defend against threats as well as detect and respond quickly should an attack occur.
Key components include next-generation firewalls, gateway antivirus solutions, intrusion detection and protection systems, identity and access management solutions and enterprise device management. Regular security assessments and threat checks also play a vital role in identifying vulnerabilities that require remediation.
Check out our Solution in Action for a detailed look at how a technology-fueled security strategy can prevent attackers from disrupting your operations.
CDW has the expertise and experience to help energy and utility companies protect critical infrastructure through smart risk management and effective security strategies.
You May Also Like
What Is GDPR, and How Does It Affect Retailers?
A major regulation went into effect this year to govern how organizations that do business in the European Union handle data. Here's what you need to know.
Why a Risk-Based Approach Yields Effective Security
A holistic assessment of threats and vulnerabilities helps an organization appropriately prioritize and mitigate its risks.
Smarter Security Addresses Evolving Threats
Artificial intelligence and data analytics are improving the performance of endpoint security solutions.
MKT25380