April 28, 2020
Getting to Know Cisco SD-WAN: Vendor Overview Series
This blog series takes an in-depth look at the software-defined WAN options in the market and their capabilities.

Over the past few months I’ve spent a lot of time working with and researching some of the top software-defined WAN vendors in the market to continue developing CDW’s Professional Services. In this blog series, I’d like to share overviews of each solution, my thoughts, strengths and areas for improvement that I think apply to each solution.
Learn more about CDW’s networking services and solutions.
I’ve written extensively about some of the key tenants of SD-WAN, the decision-making process and items to consider when deploying SD-WAN solutions. These blogs are linked here for your convenience:
- 5 SD-WAN Factors That IT Leaders Should Consider
- 7 Valuable SD-WAN Use Cases
- Winning with SD-WAN (from back in 2016)
While those blog entries cover SD-WAN from an in-depth “food-for-thought” perspective, this series will cover each vendor with a specific and technical lens.
We’ll kick off this series with Cisco SD-WAN, formerly Viptela.
Solution Overview: Cisco SD-WAN
Cisco SD-WAN is based on the Viptela OS architecture from Cisco’s acquisition of Viptela, completed in 2017. The platform maintains the core components of the solution from that time, such as vEdge routers and the vManage, vBond and vSmart controllers. Since the acquisition, Cisco has added support for ISR, ASR and CSR routers as compatible edge devices, now referred to as “cEdge.” For the purposes of this post, we’ll stick with the term “edge” to identify the edge routers in the Cisco SD-WAN solution.
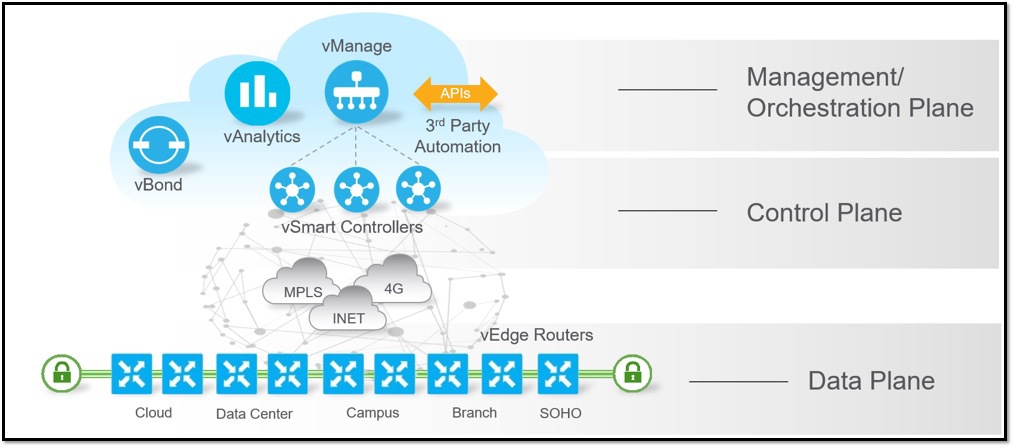
SOURCE: Cisco
Solution Elements’ Functional Roles
The elements that comprise the Cisco SD-WAN solution can all be cloud-hosted or hosted on-premises. CDW recommends the cloud-hosted solution as it is more cost-efficient than running an on-premises version, and it allows for more flexibility when engaging Cisco TAC to access the environment for troubleshooting purposes.
vBond
Orchestration platform for the solution. This element facilitates the discovery of the control elements by the vEdge router and notifies vEdge routers of their public IP, if behind network address translation (NAT).
vManage
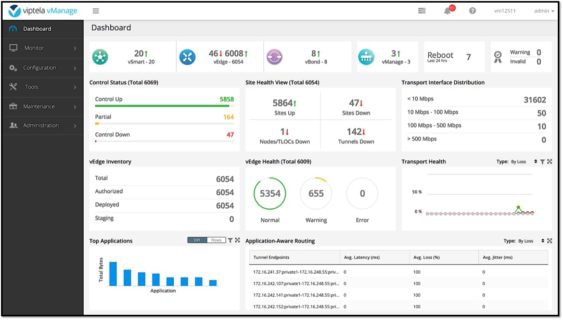
This is the management platform for the solution. The vManage is a single pane of glass that the administrator will use to configure and monitor the system. Basic troubleshooting can be performed from the vManage, but in-depth troubleshooting is still primarily done from the command line interface (CLI) of the devices.
Click to enlarge image – SOURCE: Cisco
vSmart
The vSmart acts as the control plane for the solution. It will distribute reachability (routing) information as well as security (internet key exchange, or IKE) information to the edge routers. It is also responsible for data and app-route policies, performing best-path calculation for non-ECMP (equal cost multi-path) routes and advertising the best routes to the edge.
vAnalytics
This is an optional analytics component of the solution that is only available with the cloud-hosted solution option. This module provides additional insight into the performance of the solution and can assist with future capacity planning.
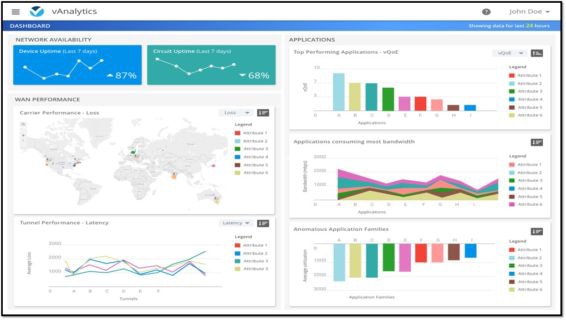
Click to enlarge image – SOURCE: Cisco
vEdge/cEdge
These are the perimeter WAN routers that provide connectivity across the SD-WAN fabric and forward across the data plane. These devices will enforce policy and execute intelligent path-based forwarding decisions. vEdge refers to the platforms running ViptelaOS, whereas cEdge refers to the platforms running IOS-XE SD-WAN. In order to implement SD-WAN capability into the existing ISR/ASR/CSR platforms, a branch of code was necessary, which is now referred to as IOS-XE SD-WAN.
Robust Security
Cisco SD-WAN offers on-box advanced security features when running on Cisco cEdge devices, such as Cisco’s Advanced Malware Protection (AMP), Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). This integration of advanced security features, enabled via license selection, provides an enterprise with a full-featured set of security capabilities across the organization from the branch edge to the enterprise edge. vManage provides an administrator with easy-to-understand contextual visibility into security vulnerabilities and threat vectors across the organization.
Cisco AMP Threat Grid is powered by Cisco Talos threat intelligence, which provides cEdges with up-to-date malware telemetry from more than 250 full-time threat researchers, four global data centers, more than 100 threat intelligence partners and millions of telemetry agents.
Cisco’s IDS and IPS systems are powered by Snort and provide an easy-to-manage ruleset that can be weighted in three different methods: toward user connectivity, a balanced approach to connectivity and security or a preference to security as opposed to connectivity. Administrators also hold the capability to whitelist certain Snort patterns in order to fine-tune the security policy to meet the organization’s needs.
In addition to the Talos- and Snort-powered feature sets, cEdges also provide a full-featured Layer 3 firewall, a Layer 7 firewall that provides application layer traffic policing and geo-based firewall features, as well as a content-filtering suite. The combined power of these security features allows an enterprise to apply end-to-end security policies across the organization rapidly, consistently and effectively.
Cisco also offers integration with Zscaler and Umbrella for hosted cloud DNS as well as cloud firewall solutions. These integrations allow customers the exceptional flexibility when implementing security policy across their organization’s SD-WAN fabric.
Segmentation
Segmentation is one of the key features of the Cisco SD-WAN solution. Network administrators now have the ability to seamlessly segment their network over the WAN easily and efficiently. By defining each network segment — referred to as a service VPN — as full mesh, hub-and-spoke, partial mesh, or point-to-point, administrators are able to apply traffic engineering at an extremely granular level. For example, you may define a PCI segment to steer traffic through a centralized hub for security inspection while your general user’s VPN may be full mesh to allow direct spoke-to-spoke communication.
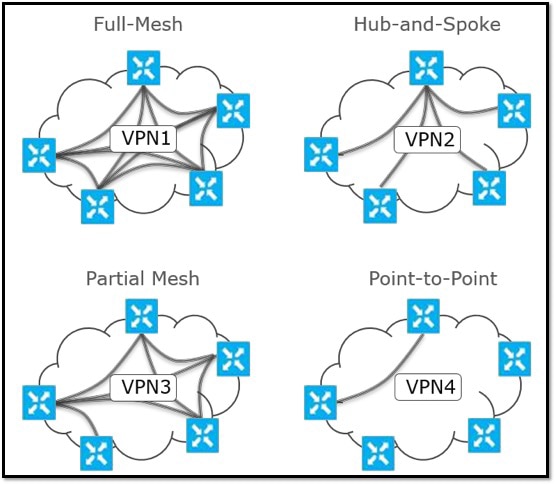
SOURCE: Cisco
Segmentation is accomplished by inserting a VPN label into the IPSec header. This ensures segmentation across all transports without any reliance on the underlying transports. The various LAN interfaces (physical or sub interfaces) are mapped into the correct VPNs and segmentation is maintained end-to-end with VRFs/VLANs on the LAN and VPNs on the WAN. The edge routers maintain complete control plane separation with different routing tables through use of dedicated management and control service VPNs.
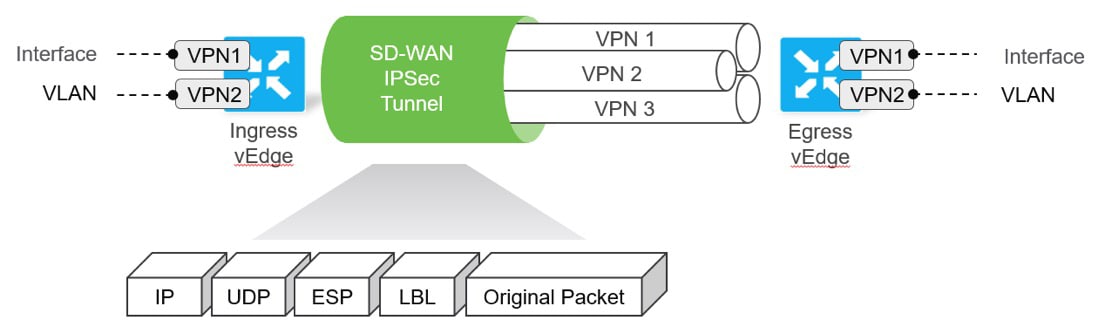
SOURCE: Cisco
Strengths and Areas for Improvement
Cisco SD-WAN is one of the solutions I’m most familiar with and I’ve seen it deployed regularly in our customer’s environments. Let’s start with what I see as strengths of the solution and then move into potential areas for improvement.
Strengths
- I believe that, long term, this solution has a lot of potential and is extremely well designed under the hood. I feel it is an outstanding “enterprise-ready” solution on the market today, allowing for the fine granularity over control and tuning. Cisco has done a lot of work to make it simpler to deploy, but it really shines in the hands of a strong engineering team.
- The built-in security integration is great. The ability to have a single box, all managed through vManage, performing SD-WAN functionality as well as advanced security functionality with optional cloud security integrations is an awesome way to get a single edge device at the branch.
- Long-term integrations are exciting. With ACI in the data center and software-defined access in the campus, the ability to link together these SDN solutions is interesting. At this point we are still waiting to see these platforms developed more fully before we decide how compelling a platform it will become.
Areas for Improvement
- When Cisco acquired Viptela the effort to integrate the SD-WAN code base into the ISR platform was rough and, frankly, the implementation is still not ideal. There have been many efforts to remedy this, and these efforts have resulted in a solution that has been improved by leaps and bounds from the initial product. We still recommend customers do their due diligence testing the Cisco routers (cEdge) running SD-WAN code before jumping into full production.
- Feature parity/integration between cEdge and vEdge is not present. Features such as Forward Error Correction and TCP Optimization do not work between them, and the platforms do not have full feature parity. Be careful when designing your solution and be sure to maintain platform standardization where possible.
- Application Quality of Experience (AppQoE) is the ability of the solution to do different types of path conditioning like Forward Error Correction, TCP optimization, Dynamic Path Select, QOS, etc. While Cisco has these features in their solution, it feels a bit lackluster compared to the competition’s implementation. Forward Error Correction on cEdge was recently added, so these gaps seem to be steadily closing.
Final Thoughts
If your organization is considering Cisco SD-WAN, it’s a great solution. I’d be especially excited about it if you had one of the following as a key requirement:
- Onboard security and other integrations: The ISR is a Swiss Army knife, and more functionality of the ISR is being brought under controls of vManage. If you need a branch in a box option, this is a great option.
- Cisco shop who is excited for future integrations: If you have solutions like ISE, SDA or ACI then the future integrations can be very intriguing.
- Advanced routing and segmentation: This solution is extremely robust in the flexibility deployment. If you’re willing to learn how to fully control it, you can tune it to do exactly what you want.
As discussed earlier, if you’re going down the cEdge route, please, do your due diligence and test that platform before fully buying in and moving into production deployment.
I believe this solution still has some growing to do, but with the solid architecture under the hood and existing enterprise features sorted out, I think Cisco SD-WAN has a bright future.