January 15, 2019
6 Game-Changing Security Features in Cisco SD-WAN
Cisco took its robust security technology on traditional IOS XE and brought it into the IOS XE SD-WAN solution.
Cisco recently released a new major update to its SD-WAN solution. This release introduced advanced security features baked directly into IOS XE SD-WAN.
The release notes can be found here and more information about the SD-WAN security features can be found here.
With SD-WAN security, Cisco was looking to solve four common branch security use cases for customers, implementing security solutions to solve for each use case.
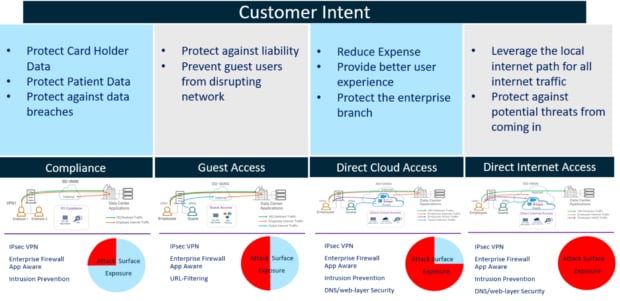
Source: Cisco
This solution is all built directly into the Cisco SD-WAN solution, meaning it is configured, provisioned, managed and reported on from vManage. SD-WAN security is supported on most Integrated Services Router/Aggregated Services Router (ISR/ASR) platforms, the Enterprise Network Compute System and the Cloud Services Router, with a few minor caveats.
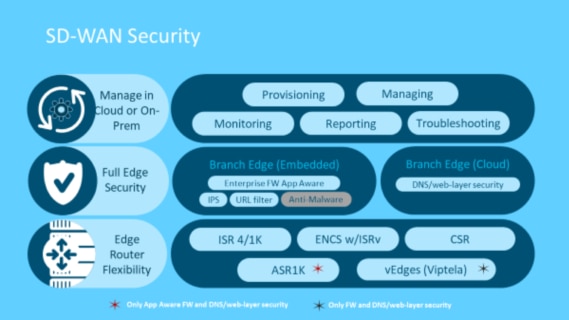
Source: Cisco
Now let’s dive into each specific security feature and explore their capabilities.
1. Enterprise App Aware Firewall
This feature is a stateful zone-based firewall. As with Cisco’s traditional stateful firewall, you can define zones and create policy between those zones. The enhancement that makes this zone-based firewall app aware is the integration with Cisco’s NBAR2 application recognition engine, which will allow you to identify more than 1,400 applications and write policy based on individual application, groups of application or category of application rather than on traditional IP and port.
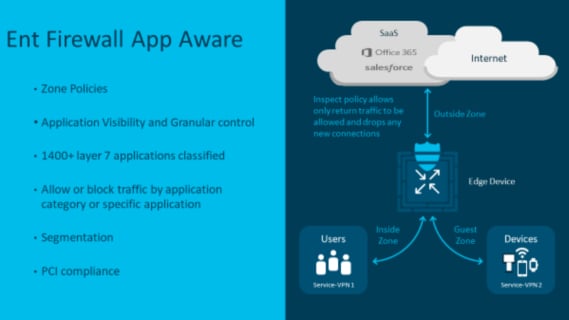
Source: Cisco
2. Intrusion Prevention System
This feature allows the Snort Intrusion Prevention System (IPS) engine to run in a container on the ISR routers. Snort is one of the most widely deployed IPS/IDS engines in the world and has been powering Cisco’s Firepower Threat Defense platform for many years. I’ve personally worked with customers to deploy Snort as their IPS/IDS solution in the past and they have been extremely happy with its performance. Signatures are provided by Cisco Talos, the company’s global threat agency. vManage can check and download new signature updates at a set interval and deploy that to all the routers provisioned for IPS.
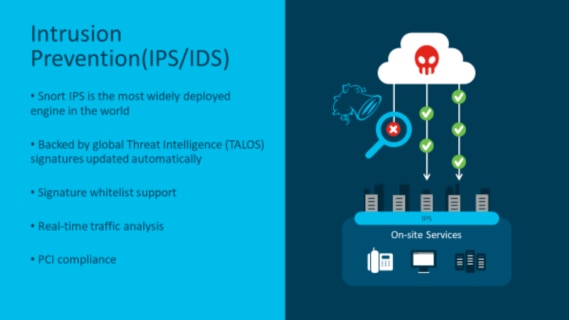
Source: Cisco
3. URL Filtering
This feature, like the Snort IPS, will run within a container on the ISR routers. When implementing this, one of the major features customers find extremely valuable is the reputation-based blocking. This is a dynamic score that is assigned to each URL. If a normally good site gets compromised with malware, its reputation score can be lowered, and your system can automatically block access.
Note: This feature has some limitations around HTTPS. While it can glean the URL before encryption and block/allow based on this information, it is unable to insert any block pages. The user will simply receive a “Page cannot be displayed” or “Connection has been terminated” message from their web browser.
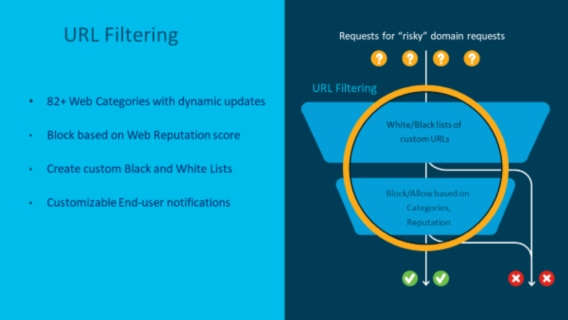
Source: Cisco
5. DNS Web Layer Security
With this feature, we are looking at the Domain Name System (DNS) layer, whereas with URL filtering, we are looking at the application layer (HTTP or HTTPS). The DNS requests are interpreted, redirected from their intended DNS server to the Umbrella cloud servers encrypted using DNSCrypt. With this DNS request, the user’s inside IP address and the device identity are also sent. Once Umbrella receives this DNS request, it will process it through your defined policy and respond with either the correct IP address of the service or any IP address redirecting the client to a block page. Umbrella also supports some advanced features such as Intelligent Proxy with options like SSL Decryption.
I really like the DNS Web Layer Security over the on-box URL filtering for three reasons. First, you don’t run into the HTTPS redirect problem as you are working at the DNS layer and not the application layer. Second, the reporting and policy creation within the Umbrella cloud is extremely robust. Third, Umbrella DNS security can be used at other points in your network, using things like the endpoint connector, which means you can write the policy once and apply it to multiple points in the network.
Note: If enforcement is required, this feature requires an active Umbrella cloud subscription.
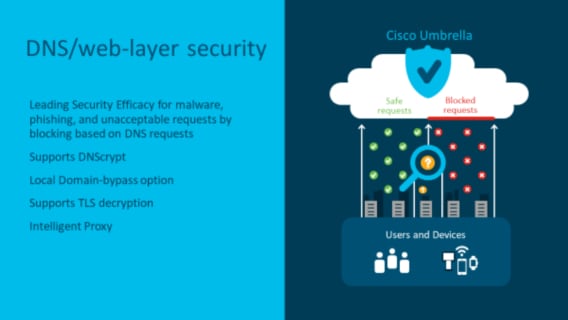
Source: Cisco
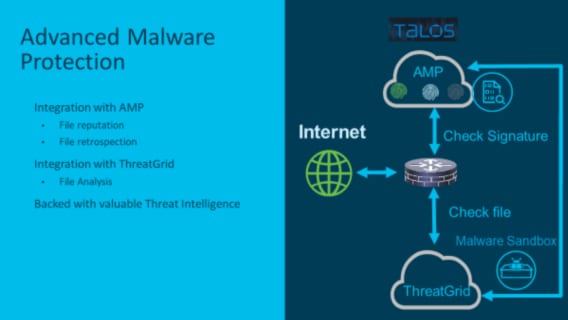
5. Advanced Malware Protection
AMP will allow the router to look at files downloaded from the internet over protocols such as HTTP, SMTP, IMAP, POP3, FTP and SMB. As the router observes the file, it will generate a SHA 256, which will be sent to the Talos AMP Cloud where the SHA 256 is compared against AMP’s database. It will then return a file disposition informing the router of the file’s maliciousness. If the AMP database does not have a record for the file, this is where ThreatGrid comes in.
ThreatGrid is an optional add-on to AMP. If the file does not have a matching SHA 256 in the AMP Cloud, the router will store the file temporarily and send it to the ThreatGrid cloud sandbox where it can be executed, checked for malware and have a disposition returned. ThreatGrid will then send this new SHA 256 hash to the AMP database for future queries.
Note: This feature will not work with encrypted files, such as HTTPs, as the system currently does not support SSL decryption.
Source: Cisco
6. Licensing
I’m extremely happy Cisco has made the decision to include the SD-WAN security features in the DNA Essentials licensing level, with the exception of ThreatGrid. This means that most customers will have the ability to use these features. The only additional licensing that would be required is Umbrella.
SD-WAN Security Features Really Measure Up
I’ve had the opportunity to set this all up in the CDW lab and kick the tires. Let me say, I’m really impressed. These new integrated security features really are game changers. I’ve done tons of SD-WAN implementation work and the number one benefit customers gained was moving to a limited or full direct internet access model with geolocated DNS. These new SD-WAN security features really make it easy for customers to move to these new types of internet/cloud app egress models. The configuration of all these features through vManage is intuitive and easy to understand. Through policy, you can then simply apply this security policy to your desired branches. Then, if there is a change you want to make, it’s done centrally and applied to all relevant branches. Reporting is also fully centralized.
The only thing I’d really like to see Cisco improve is the reporting. Currently, within vManage, the App Aware Firewall, IPS/IDS and URL filtering reporting are quite basic and there is no way to do scheduled reporting. However, if you can use the Umbrella integration, the reporting from that system is quite robust.
If your organization is looking at Cisco SD-WAN, I’d highly recommend considering the security feature set in your design as it brings many compelling features that take your SD-WAN deployment to the next level.