October 09, 2019
How to Make Office 365 Even More Secure — Part 1
Make these three tweaks to take full advantage of Microsoft's security capabilities.

Cybersecurity — one word that can inspire many different tactical approaches depending on its definition. If you feel overwhelmed by the idea of defining cybersecurity and developing a plan for its inclusion within your environment, then you’re not alone. Many organizations have started down the path of addressing exposure points, defining red and blue teams, and following NIST’s Cybersecurity Framework, but we still see news every day on the latest company to receive the brunt of a hacker’s keystrokes.
Ironically, cloud services are intended to reduce our exposure and allow our security teams to sleep better at night. While cloud has enabled us to make tremendous strides in the security space and opened up many new security capabilities and features, there is still evidence that we have a lot more to do. As organizations continue their move toward cloud and Office 365, it is important to start taking advantage of many of the new security capabilities that Microsoft has made available and continues to improve. With this need in mind, we are going to share several easy steps to help your organization move toward a more secure Office 365.
1. Protect Your Synced and Cloud Identities
It probably comes as no surprise that syncing your Active Directory objects and passwords to Office 365 is quite simple to do. However, what we find is that many organizations will ultimately stop with the default installation of Azure AD Connect, enable password synchronization, and then call it a day. It just works, and because the passwords are encrypted, everything is secure, right?! While password synchronization is, in fact, a secure mechanism for controlling and managing passwords, CDW always recommends enabling a secondary security check for users. The solution is multifactor authentication.
Enabling MFA is simple, and it can dramatically reduce the likelihood of users having their identities and passwords compromised.
According to the 2019 Data Breach Investigations Report from Verizon, it is estimated that 80 percent of confirmed data breaches involve weak, default or stolen passwords. MFA is a fantastic deterrent for these issues. If your organization requires time to enable this feature fully, we recommended that, at a minimum, you enable MFA features for privileged accounts with administrative access or for accounts that have access to sensitive information, such as e-discovery data, personally identifiable information (PPI), private health information (PHI) and so on.
2. Lock Down Exchange Online, Especially If You Have a Hybrid Deployment
Exchange Online is the most widely used workload in Office 365. One of the immediate benefits of using this service for email is that Office 365 Software as a Service workloads are generally more secure than on-premises environments simply due to the incredible amount of resources, time and requirements needed to support and secure such a robust platform. Microsoft also has more than 3,500 security professionals — all vetted through significant personnel screening and controls — who watch the infrastructure 24/7. However, these professionals aren’t enabling security polices for you at the application layer. There are a few simple steps you can immediately take to reduce or eliminate some of the common security exposure points we’ve seen in Exchange Online.
- Turn off email forwarding to external email addresses. This action closes a loophole that would allow a malicious actor or user to forward company email data to an external email account. External email accounts cannot be controlled by your organization, and any content included in these emails is now accessible if that user leaves your organization.
- Turn on outbound spam, malware and ransomware policies. These settings can save your company the headache of a damaged email reputation by notifying administrators that a user’s workstation may have been compromised. These policies will check for malware kits or bots that leverage workstations as a springboard for sending malicious or misleading spam from your internal network. A bad email reputation could immediately impact your business and bottom line by limiting the ability to communicate effectively with external partners.
3. Embrace and Enhance Office 365 Cloud Auditing
New Office 365 tenants have audit logging enabled by default, but tenants enabled prior to January 2019 have not been enabled for this automatically. We highly encourage all organizations to take a moment to review and validate that all admin actions as well as all mailboxes within your Office 365 tenant are enabled for auditing. The process to enable these features, or check to see if they are already enabled, is extremely simply and fast. Browse to your Security & Compliance Center and then Search > Audit Log Search. If you see the below message, you need to click Start recording user and admin activities to enable these security features.
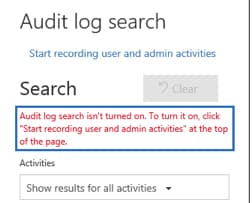
Enabling these features will allow you to start logging the actions of administrators as well as end-user mailbox actions. If your organization is ever in a situation where an audit trail is needed to find out who made an administrative change in Office 365, or whether someone with permissions is accessing mailboxes maliciously, you now can easily report on this activity.
You’re probably thinking “Ok, now we’re in good shape, no further actions within the audit space are needed and we can move on.” Not so fast. Did you know that the average time to identify an internal breach is more than 200 days? Are you also aware that the default audit log retention for an E3 license is only 90 days? If your organization requires audit logging and reporting to be available for longer than 90 days, work with your CDW licensing specialist to upgrade to an E5 licensing package, which allows for audit log retention of more than 90 days. If E5 licensing is not a viable option, another recommended method would be to export these logs and store them for future consumption by your compliance and security teams. You could also consider leveraging Microsoft’s most recently released security information and event management (SIEM) cloud solution, Azure Sentinel.
Knowing that audit logging is enabled is certainly comforting, but it’s also important to regularly review these logs to ensure that your organization is protected. One way to orchestrate this would be to leverage a product like Microsoft Teams. Create security-focused teams and a corresponding Teams channel, add Planner as a tab and assign a weekly task to key security stakeholders (IT Managers, etc.) that reminds them to review audit logs for unusual activity.
Read the conclusion of our Office 365 security tips in part two of this post.
Learn more about how CDW can assist you with your Microsoft solutions and services.

Josh Walters
CDW Expert

